Are you tired of the limitations imposed by firewalls when trying to access your remote IoT devices? Overcoming these hurdles is not just possible, it's crucial for maintaining both the functionality and security of your connected systems.
Whether you're a novice venturing into the world of IoT or a seasoned professional seeking to optimize your existing setup, this comprehensive guide aims to provide valuable insights into navigating the complexities of remote device access. We'll delve into the intricacies of firewalls, explore the nuances of port forwarding, and offer practical solutions to ensure seamless connectivity, no matter your level of expertise.
Remote IoT (Internet of Things) devices have fundamentally reshaped how we interact with technology. The ability to monitor and control systems remotely is no longer a luxury but a necessity in a world increasingly reliant on interconnected devices. From smart home automation to sophisticated industrial equipment, the demand for secure and reliable remote access is at an all-time high. This article serves as your compass, guiding you through the often-treacherous waters of firewall restrictions and offering clear, actionable steps to achieve uninterrupted access to your remote IoT devices.
Here's a table to understand the context of the topic:
| Category | Details |
|---|---|
| Concept | Remote IoT Access |
| Challenge | Firewall Restrictions & Router Settings |
| Goal | Secure and Uninterrupted Access to IoT Devices |
| Platforms Mentioned | macOS, Windows (for comparison), Routers |
| Techniques Discussed | Firewall Configuration, Port Forwarding, MAC Address Filtering |
| Target Audience | Beginners & Advanced Users of IoT systems |
Let's begin with a fundamental understanding: IoT, or the Internet of Things, refers to the vast network of physical devices embedded with sensors, software, and connectivity that enables them to exchange data. These devices range from simple sensors in your home to complex machinery in industrial settings. The ability to remotely access and manage these devices is key to their utility. However, accessing these devices remotely, particularly when they are behind firewalls and routers, is rarely straightforward.
One of the initial challenges is understanding the role of a firewall. Think of a firewall as a digital gatekeeper, diligently scrutinizing all incoming and outgoing network traffic. Its primary purpose is to protect your network from unauthorized access and malicious threats. While essential for security, firewalls can also inadvertently block legitimate traffic, including the communication required to access your remote IoT devices. To effectively use remote IoT, you must understand how to configure your firewall to allow the necessary traffic through. This often involves configuring "exceptions" or "rules" that permit specific types of data transmission.
Beyond firewalls, the router itself presents another set of obstacles. Routers are the essential devices that connect your local network to the Internet. They assign IP addresses, manage network traffic, and, crucially for our discussion, can also act as a firewall. Understanding your router's settings is critical for enabling remote access. Many routers employ a feature called Network Address Translation (NAT), which translates the private IP addresses of devices on your local network into a single public IP address visible to the Internet. This translation process, while useful for security, can make it difficult for external devices to initiate connections to your IoT devices. Here, port forwarding plays a vital role.
Port forwarding is the process of configuring your router to direct incoming network traffic from a specific port (a virtual doorway) on the router's public IP address to a specific device and port on your local network. By "forwarding" these ports, you essentially create a pathway that allows external devices to reach your remote IoT devices. However, it is essential to configure this correctly. The wrong configuration can compromise your network security, while incorrect settings will simply prevent the devices from connecting.
Now, consider the impact of Mac Address Filtering. Routers often offer the option to filter network access based on the Media Access Control (MAC) address, a unique identifier assigned to each network device. While MAC address filtering can enhance security by preventing unauthorized devices from joining your network, it can also impede your ability to connect to remote IoT devices if not properly configured. One of the simplest ways to resolve this issue is to temporarily disable Mac address filtering to test and enable the configuration.
Here's a practical guide to accessing your remote IoT devices on a Mac. We'll begin with some preliminary steps that are critical before you begin:
- Understand your network architecture: Identify all your IoT devices, their IP addresses (both static and dynamic), and the ports they use for communication. Static IP addresses are highly recommended for your IoT devices, as these addresses will not change.
- Know your router's model and IP address: This information is critical for accessing its configuration interface. The default gateway IP address is usually 192.168.1.1 or 192.168.0.1. Check your routers manual if necessary.
- Secure your network: Implement strong passwords for your router and Wi-Fi network to prevent unauthorized access. Regularly update your router's firmware to patch any security vulnerabilities.
Next, we'll configure your Mac's firewall.
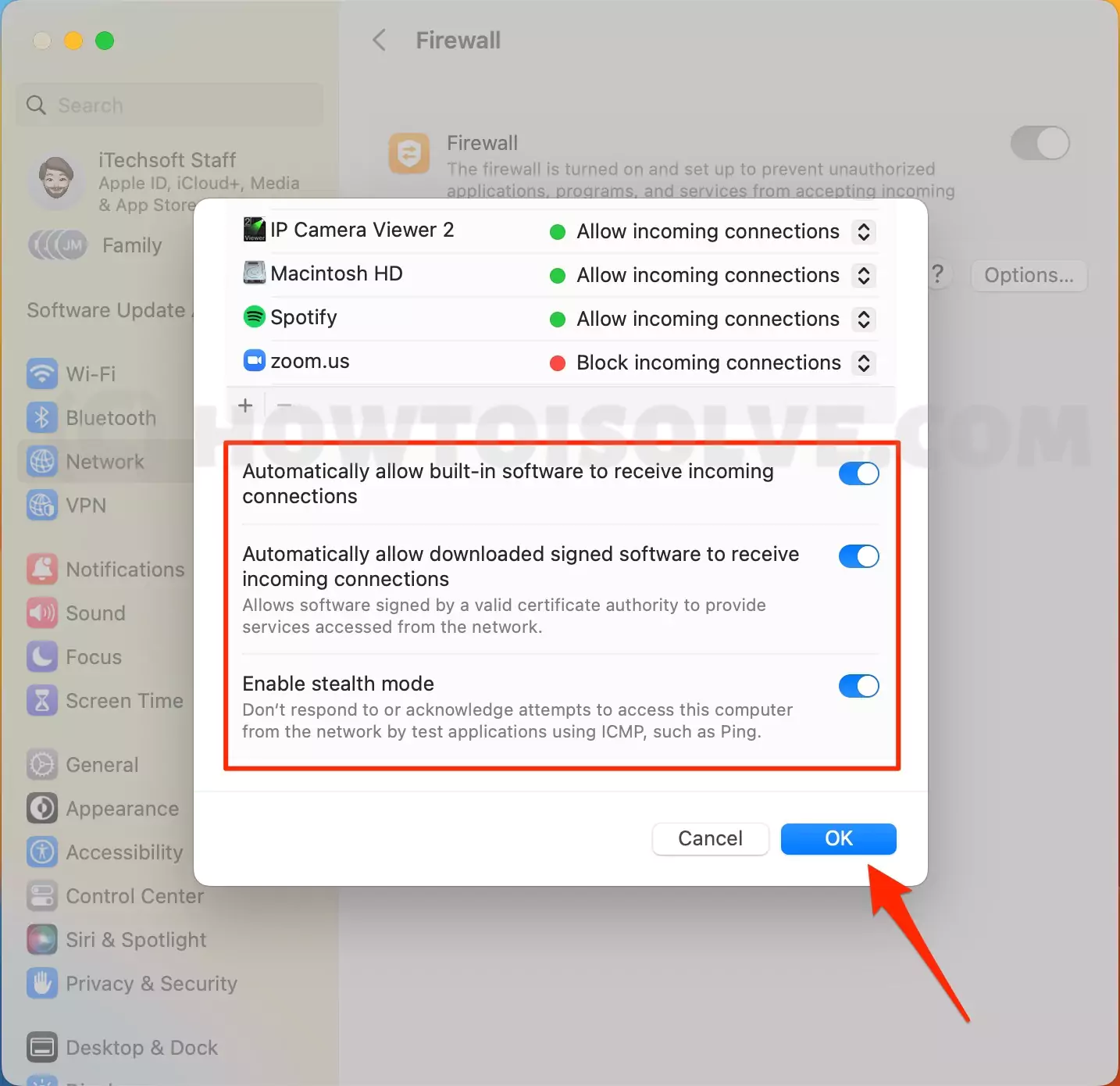
- Access System Preferences: Go to the Apple menu (top-left corner) and select "System Preferences." Then, click on "Network."
- Select your network connection: In the Network settings, choose the network interface you're using (e.g., Wi-Fi or Ethernet).
- Click "Advanced": This will open a new window with several tabs.
- Select the "Firewall" tab: This is where you can configure your firewall settings.
- Enable the firewall: If your firewall is not enabled, click the "Turn On Firewall" button.
- Configure Firewall options: Click on "Firewall Options..." and add a custom rule to allow connections to your IoT device's port.
- Check for Stealth Mode: Verify that Stealth Mode is disabled. Stealth Mode can prevent incoming connections, even if the specific ports are open.
Now, let's address the router configuration:
- Access the router's admin interface: Open a web browser and enter your router's IP address (usually 192.168.1.1 or 192.168.0.1) in the address bar. You'll be prompted for your username and password.
- Locate the port forwarding section: The exact location varies depending on your router model. Look for sections labeled "Port Forwarding," "Virtual Servers," or "Applications & Gaming."
- Create a new port forwarding rule:
- Service Name: Give the rule a descriptive name (e.g., "RemoteIoTDevice").
- Protocol: Choose the protocol your IoT device uses (usually TCP, UDP, or both).
- External Port: Enter the port number that external devices will use to connect to your IoT device (e.g., 8080).
- Internal Port: Enter the port number your IoT device is using (e.g., 8080).
- Internal IP Address: Enter the local IP address of your IoT device.
- Save the changes: Apply and save your port forwarding configuration.
- Disable MAC address filtering (Optional): For simplicity, you can disable MAC address filtering, at least during the initial setup, to eliminate this as a potential point of failure.
After completing these steps, you'll need to test your connection to verify it's working correctly. You can use an online port checker, available through various websites, to verify that the ports you have forwarded are open. Enter your public IP address (you can find it by searching "what is my IP address" on any search engine) and the port number you forwarded.
Troubleshooting is a crucial aspect of managing any technology system. If you encounter any difficulties during the setup process, there are several common issues to be aware of:
- Incorrect IP Address or Port Numbers: Double-check all IP addresses and port numbers to ensure they are accurate.
- Firewall Blocking Traffic: Ensure your Mac's firewall isn't blocking incoming traffic on the forwarded port. Temporarily disable the firewall to test and re-enable once you've confirmed connectivity.
- Router Configuration Issues: Make sure you've entered the correct port forwarding information in your router's admin interface. Also, ensure the router's firmware is up-to-date.
- ISP-Level Firewalls: Some Internet Service Providers (ISPs) employ firewalls that can also block incoming traffic. Check if your ISP blocks the ports your IoT devices require.
- Double NAT: In some cases, you might have two routers, creating a Double NAT situation. This can complicate port forwarding.
- MAC Address Filtering: Ensure the MAC address of your IoT device is allowed through your router's MAC address filtering, if you're using it.
When working with remote access solutions, security should be paramount. Here are some crucial tips to enhance the security of your remote IoT setup.
- Use Strong Passwords: Implement strong, unique passwords for all your devices, including your router, IoT devices, and any remote access software. Use a password manager to keep them secure.
- Enable Encryption: Utilize encryption protocols like SSH or TLS to secure the communication between your devices and the remote access client.
- Keep Firmware Updated: Regularly update the firmware on your router and IoT devices to patch any security vulnerabilities. This is crucial to avoid potential exploits.
- Use a VPN: Consider using a Virtual Private Network (VPN) to encrypt all your internet traffic, including remote access connections. A VPN provides an additional layer of security.
- Implement Two-Factor Authentication (2FA): If available, enable 2FA on your remote access accounts to add an extra layer of security.
- Monitor Network Traffic: Regularly monitor your network traffic for any suspicious activity. Use network monitoring tools to detect any unauthorized access attempts.
- Segment Your Network: If possible, segment your network to isolate your IoT devices from your main network. This can limit the impact of a potential security breach.
- Limit Remote Access: Restrict access to your remote devices to only authorized users and only when necessary.
By following these steps, you'll be well on your way to securely accessing your remote IoT devices. Remember, the world of IoT is constantly evolving. Stay informed about the latest security threats and best practices to ensure the continued integrity of your connected systems.
While understanding the fundamentals of remote IoT access is essential, it's important to note that this process can sometimes be challenging. Factors like the specific router model, ISP restrictions, and the underlying complexity of network protocols can all introduce complications. The steps outlined above provide a solid foundation; however, in some instances, you may need to consult the documentation for your specific devices or router or seek expert assistance.
Beyond the technical aspects, consider the broader implications of your IoT setup. As more and more devices come online, the potential for data breaches and security vulnerabilities increases. This makes it crucial to adopt a proactive approach to security, from the very beginning. Regularly evaluate the security posture of your entire system, and be prepared to adapt to new threats as they emerge.
As more businesses and individuals rely on IoT devices, understanding how to configure these tools securely is no longer an option but a necessity. By mastering these techniques, you empower yourself to unlock the full potential of remote device management. You can safely connect to a device on a private or mobile network, regardless of NAT router or firewall restrictions. Utilize SSH or remote desktop (VNC, RDP) for a secure connection.
In summary, accessing remote IoT devices securely behind firewalls requires a multi-faceted approach. It involves understanding firewalls, properly configuring port forwarding, and adhering to best practices for network security. By taking the time to understand these concepts and following the steps outlined in this guide, you can confidently create a secure and reliable remote access solution for your IoT devices.